14) which of the following are breach prevention best practices
Vulnerability assessment is the process intended to identify classify and prioritize security threats and. Properly configure the cloud.

Alarming Cyber Statistics For Mid Year 2022 That You Need To Know
11 Which of the following are breach prevention best practices.

. Companies that leveraged artificial intelligence machine learning. Identify areas that store transmit collect or process. Identity sensitive data collected stored transmitted or processes.
To effectively prevent or mitigate the risk of a data breach you should be continually monitoring your assets. Which of the following are breach prevention best practices. All of this above.
Which of the following are breach prevention best practices. All of the above You can help prevent a breach by accessing only the minimum amount of PHIPII necessary and by promptly. What are best practices.
A strong password will be at least 12 characters long including at least one upper case letter number. 2 data breach landscape data breaches cost companies an average of 221 per. Using strong passwords is an essential part of preventing breaches.
Where a breach has taken place companies may need to notify individuals as well as face negative impact on the companys brand and customer loyalty. The following are high-level best practices for preventing breaches. Logoff or lock your workstation when it is unattended.
Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your. Invest in security automation. Which are breach prevention best practices.
Which are breach prevention best practices. Which of the following are breach prevention best practices. Properly configure the cloud.
All of this above correct 3 Which of the following are true statements about limited data sets. Promptly retrieve documents containing PHIPHI from the printer. The following are high-level best practices for preventing breaches.
Best practices for breach prevent are. Awasome 14 Which Of The Following Are Breach Prevention Best Practices 2022. The following are high-level best practices for preventing breaches.
All of this above answer Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or. Phases of a data breach reported data breaches data breach laws best practices. 30 Best Practices for Preventing a Data Breach.
Identify users with access to sensitive data Although. Implementing encryption standards and backup policies to decrease risks and make sure that software is. 2 Which of the following are breach prevention best practices.
Invest in security automation. Invest in security automation.

Orca Security Launches Industry S First Cloud Risk Encyclopedia To Provide Ongoing Education For Cloud Security Best Practices Business Wire
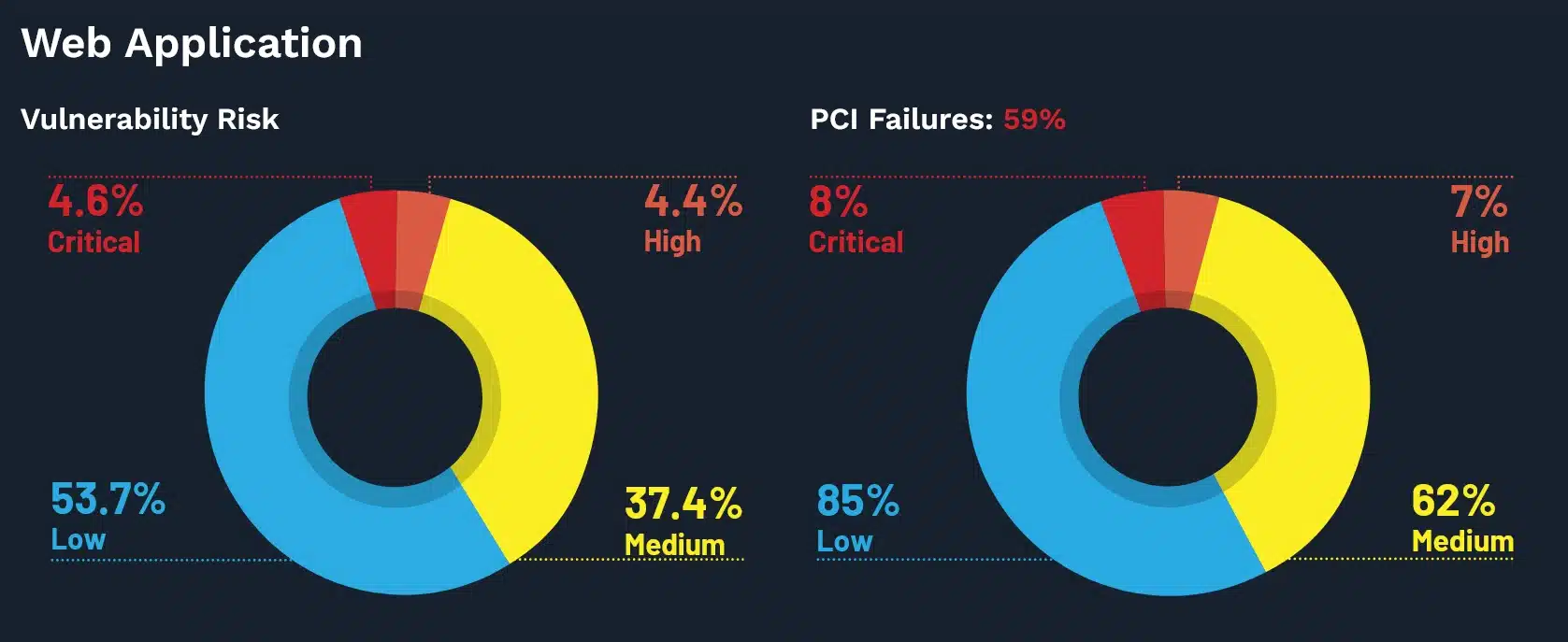
25 Cyber Security Vulnerability Statistics And Facts Of 2022

14 Ways To Avoid Linkedin Identity Theft Cybertalk 2022
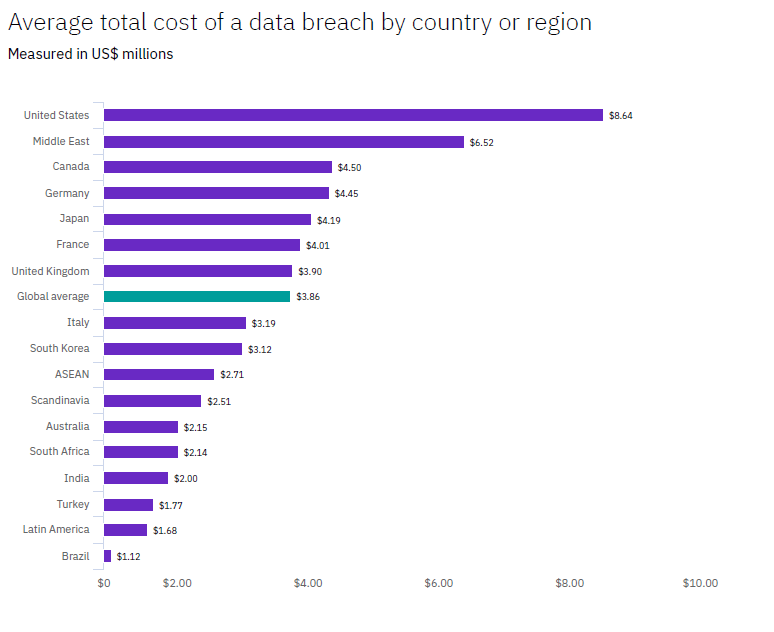
How Much Can Data Loss Cost Your Business Acronis

2021 Data Breaches Have Already Exceeded All Of 2020 Id Agent

Top Best 30 Active Directory Security Best Practices Checklist In 2022

Top Best 30 Active Directory Security Best Practices Checklist In 2022

Privacy Breaches Impact Notification And Strategic Plans Lexology
Assume Breach Mentality Vs Supply Chain Attacks In 2022 Upguard

Alarming Cyber Statistics For Mid Year 2022 That You Need To Know

Top Best 30 Active Directory Security Best Practices Checklist In 2022

Alarming Cyber Statistics For Mid Year 2022 That You Need To Know
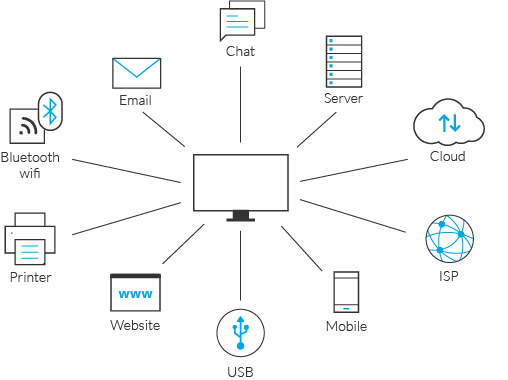
What Is Data Loss Prevention Dlp Data Leakage Mitigation Imperva

Data Protection Laws And Regulations Report 2022 Usa

Penetration Test Steps 5 Phases And Process

Working From Home Cyber Security Risks Best Practices Nordlayer

Assume Breach Mentality Vs Supply Chain Attacks In 2022 Upguard

What Is A Man In The Middle Attack Mitm Attack Prevention

Cyber Terrorism What It Is And How It S Evolved Maryville Online